Proposed in 2017 by Gavin Wood, co-founder of Ethereum, PoA is an alternative consensus mechanism that depends on known and reputable validators to create blocks, thereby providing computational power to a network and does not require any mining activity. The proof of authority consensus algorithm is evolving as one of the most efficient versions of blockchain technology. PoA is being used to track supply chains by market leaders like Walmart and GE Aviation, and Microsoft has created a whole string of PoA-based industry products.
What is Proof of Authority?
PoA algorithm depends on the reputation of the parties in a blockchain network and is majorly used in private blockchain networks. It enables relatively faster transactions using a Byzantine Fault Tolerance (BFT) algorithm, with identity as a stake. The system is extremely scalable due to the minimized number of block validators; thus, Proof of Authority can also be incorporated in applications such as supply chains and trade networks on the ground that the real identities of the nodes are verified and trusted. The POA concept allows businesses to protect their privacy while leveraging the advantages offered by blockchain technology.
How does Proof of Authority work?
In concept, Proof of Authority works on the following pre-requisites
- The validators are required to be formally identified on-chain
- Eligibility is based on a set of pre-defined criteria such as association with the organization, good reputation, credibility, etc
- Complete harmonization and alignment to defined procedures for the creation and validation of blocks on the network
The structure of Delegated Proof of Stake and Proof of Authority are similar in terms of very few validators. Mainly, the difference is in selecting the validators. In Delegated Proof of Stake, the validators are chosen by the community. In the Proof of Work, the validators are selected through a structured method.
Related article: How to choose the right consensus protocol for permissioned blockchain networks
The major difference between the PoS and PoA consensus is that the PoA is about the identity of the validators. This implies that reputation is more important than possession in the system. The network relies on a set of pre-approved validators that verify transactions and build new blocks.
How are Block Leaders selected?
As the network implementing the Proof of Authority algorithm stakes identity, the entities aspiring to become authorities must voluntarily disclose their identity and comply with the pre-specified criteria to be considered trustworthy. The validator candidates must also undergo a selection process, proving their long-term commitment to the network. They should also be ready to invest and put their reputation at stake during the selection. This is why the PoA consensus is preferable for private networks rather than public blockchains.
Finally, the process for the selection of authorities must comply with certain standard rules so that all candidates have equal chances for higher positions. The validators get rewards as the candidates reveal their identities and prove who they are with government-issued documents. It is to be noted that only a minimal number, i.e., around 25 authorities, should be validating transactions and blocks on the chain. This ensures that the proper efficiency and security are provided to the network.
The process of block creation may vary based on the particular implementation. It is mostly explained in Authority Round and Clique. The Clique is divided into “epochs,” each starting with a special block that lists the validators for the next set of blocks. Many validators suggest a block in Clique, not only the block leader. The first form of PoA is known as Authority Round or AuRa.
- In the initial step, a leader creates a block and broadcasts the block to other validators.
- In the second phase, validators distribute the block they received to one another.
- If everyone in the ecosystem receives the same block, the block is accepted, and the process initiates with a new block leader. If they don’t, a vote will be held to determine if the block leader is malicious.
- If most other validators believe the block leader is a malicious actor, they are removed and lose their block-creation rights. The process just restarts if this is not the case.
Why should you implement Proof of Authority?
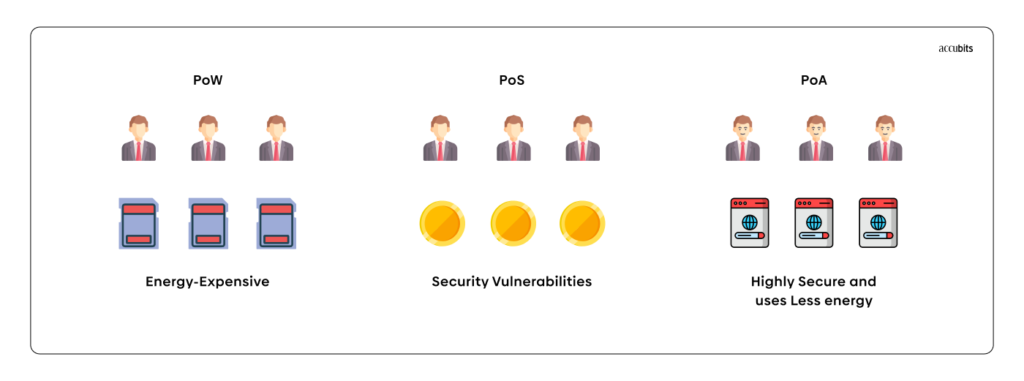
The Proof of Authority algorithm has numerous pros over others in terms of simplicity of the validation process, reduction of power to maintain the network, and additional benefits such as:
No sophisticated hardware
Unlike the PoW consensus algorithm, which requires high-performance hardware to solve the complex mathematical tasks necessary for validating blocks, PoA does not need to solve puzzles to ensure a stable connection between nodes. Thus, the validators do not require special equipment to sustain the network.
Better transaction rates
PoA enhances the speed of transaction validations by the authorities. All blocks are generated in a predictable sequence based on the number of validators, and thus a higher transaction rate than Proof-Of-Work or Proof-Of-Stake can be seen in the Proof-Of-Authority algorithm.
Tolerance to attacks
PoA is relatively more resistant to attacks than the PoW consensus, as the network cannot be compromised by a single user who manages to generate 51% of the computational power. It is extremely troublesome for phishers to acquire control of more than 51% of authorities that aren’t connected directly. In addition, as the nodes are pre-authenticated, if one of them is unavailable, the network can exclude it from the validation process.
Environmental friendliness
PoA also has the advantage of being more environmentally friendly than Proof-of-Work-based algorithms, as block validators aren’t competing to find block hashes. Therefore, they do not need to use electricity on processor cycles to find the correct hash per block.
Where can you apply Proof of Authority?
PoA Algorithms are optimally feasible for enterprise-level networks such as blockchain consortiums and other private networks, where a significant level of trust already exists among the participants owing to the number of validators being kept at a minimum. The following are some of the prominent use cases of PoA algorithms.
Proof of Authority for Testnets
Testnets can be considered as one of the most important use cases when it comes to PoA implementation. A PoA consensus is ideal for providing a controlled environment to test features before they are released on the mainnet. Proof of Authority is used on three of Ethereum’s testnets: Kovan, Goerli, and Rinkeby. Meanwhile, Polkadot, one of the most popular blockchain protocols today, began as a PoA network in beta before transitioning to a PoS network for general release.
Alternative to sidechain
PoA can also serve as an alternative for a sidechain, a type of blockchain that runs parallel to a parent blockchain and is connected to it via a two-way bridge. The POA Network is an example of a public Ethereum sidechain that relies on pre-selected validators whose identities are public and verifiable.
Proof of Authority based Online games
A prominent use case of PoA can be seen in the development of online games aimed at high scalability. The advantage for gamers here would be the minimal transaction cost offered by PoA-based solutions. As the PoA network is three times faster than Ethereum, the server workload is significantly reduced.
Related article: What are Move-to-Earn NFT Games and are they profitable?
VeChainThor
VeChainThor is another and the most celebrated example of PoA. It is a public blockchain that derives its value from activities carried out by ecosystem participants to solve real-world economic challenges.
Supply Chains
PoA can be extremely useful for supply chain tracking and verifying goods in the logistics sector. The PoA algorithm’s transparency and speed would aid logistics operators in tracking any commodities in transit in real-time for maximum efficiency of deliveries.
Energy
Applications of PoA can also be seen in the energy sector. For example, Energy Web Foundation (EWF) is launching its blockchain for several major energy companies, such as Mercados Electricos. The application will allow companies to increase energy efficiency and ensure regulatory compliance significantly.
We can see a role for blockchain in enabling decentralized energy trading. Suppose consumers begin to generate more energy on their solar roofs than they need. In that case, they will be able to sell the surplus through a distributed registry system at real-time regulated prices.
Conglomerates and Corporate
PoA algorithms provide a mechanism that exempts administrators from complex computing operations, thus considerably cutting down electricity consumption and increasing network profitability. Organizations ready to implement PoA in their processes might lose some degree of decentralization. Still, they will be able to retain the benefit of efficient multi-party collaboration, which will prove useful in the long run.
Closing thoughts
In conclusion, a blockchain-based on Proof-of-Authority is an efficient, centralized system, uses less power, and is one of the most feasible options available today for private blockchains. Because of its efficiency, audit, and coordination, this technology will likely become important in businesses, even if trust between players is difficult to develop. Proof of Authority could be viable for corporations looking to implement in-house blockchain solutions to increase productivity. The reliability of a validator’s identification strikes at the core of the reputation process. This way, all validators follow the same protocol for the integrity and reliability of the system.